DMARC Study: Most Higher Ed Domains Not Protecting E-mail Security Fully
- By Kristal Kuykendall
- 03/09/23
New research shows that an overwhelming majority of education institutions in the United States have incorrectly configured e-mail security settings and as a result are more susceptible to phishing and spoofing threats.
The report from e-mail security provider EasyDMARC reviewed the security policies of .edu e-mail domains, which are assigned to 1,930 U.S. higher education institutions. The researchers found that only 152 — or a mere 7.8% — of the country’s .edu domains have correctly implemented and configured security policies to flag, report, and remove outbound phishing e-mails.
The survey reviewed the deployment of the Domain-based Message Authentication, Reporting and Conformance (DMARC) standard among .edu domains, first published in 2012. The standard enables the automatic flagging and removal of receiving e-mails that are impersonating senders’ domains, which EasyDMARC described as “a crucial way to prevent outbound phishing and spoofing attempts.”
While 58% of U.S. .edu domains had implemented the DMARC standard, more than 9 in 10 were not completely implemented in a manner that deploys all of DMARC’s capabilities, EasyDMARC said in its report, “DMARC Guide for Education IT Staff.”
Key Findings of the EDU Domain Study
Among the .edu domains that had implemented DMARC, 848 or 76% were using DMARC only to monitor outgoing e-mails impersonating legitimate domains.
-
199 or 18% of DMARC-using .edu domains were only slightly more complete in their implementation, having also set their policies to send impersonating e-mails to quarantine.
-
152 institutions — 7.8% of all .edu domains, equaling 14% of DMARC-using .edu domains — had DMARC set to automatically reject site e-mails impersonating their domain.
The institutions not using the full DMARC capabilities “leave users vulnerable to still receiving phishing e-mails … and creates a substantial risk for ransomware attacks, fraud, and data breaches,” said the report.
“It’s very concerning to see that less than one in ten U.S. higher ed institutions have adopted adequate protection against (phishing and spoofing) attacks by adequately implementing a DMARC solution,” said EasyDMARC CEO Gerasim Hovhannisyan.“With many organizations moving to cloud-based e-mail ecosystems, it’s likely that many educational institutions are finding it difficult to find a way to implement DMARC that can operate seamlessly alongside their SaaS solution stack. For vendors and service providers to educational institutions, these findings should be a wake-up call regarding the massive security gap that needs to be filled with cloud-native DMARC solutions.”
The report noted that in the first six months of 2022, the education and research sector saw a 44% increase in cyberattacks globally, and according to Checkpoint’s 2022 Cyber Attack Trends Mid-Year Report, education was the most targeted industry for the period.
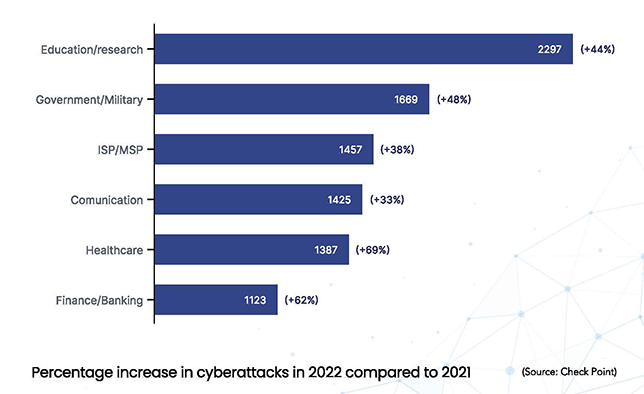 The Checkpoint data also shows that e-mail-delivered attacks comprised 89% of all “in the wild” cyberattacks during that period. Also widely seen were malicious “Microsoft documents” attachments delivering malware — representing 61% of all malware attacks.
The Checkpoint data also shows that e-mail-delivered attacks comprised 89% of all “in the wild” cyberattacks during that period. Also widely seen were malicious “Microsoft documents” attachments delivering malware — representing 61% of all malware attacks.