Report: Only Half of Ransomware-Compromised Data Will Be Recovered
During a ransomware attack, organizations can expect 41% of data to be compromised — and on average, only 57% of compromised data will be recovered, according to the 2024 Ransomware Trends Report from Veeam Software. That leaves organizations vulnerable to substantial data loss and negative business impact as a result of a cyber attack.
Third in an annual series, the report is based on a survey of 1,200 respondents including CISOs or similar titles and others whose organizations suffered at least one ransomware attack in 2023, and is designed to assess different perspectives in the fight against ransomware.
Kkey findings of the report as presented by Veeam include:
- Cloud and on-premises data are just as easily attackable: Surprisingly, there was no significant variation between how much data was affected within the data center vs. data within remote offices/branch offices or even on data hosted in a public or private cloud. Meaning that as you've easily expanded your hybrid-cloud architecture to enable access to the users, that data is equally vulnerable to attacker. Hence, ensuring a comprehensive backup and recovery strategy across all those hybrid workloads is a must.
- Most organizations risk reintroducing infections: Alarmingly, almost two-thirds (63%) of organizations are at risk of reintroducing infections while recovering from ransomware attacks or significant IT disasters. Pressured to restore IT operations quickly and influenced by executives, many organizations skip vital steps, such as rescanning data in quarantine or a "sandbox," causing the likelihood of IT teams to inadvertently restore infected data or malware.
- Organizations must ensure recoverable data: As a "lesson learned," respondents of prior cyberattacks now recognize the importance of immutability with 75% of organizations now utilizing on-premises disks that can be hardened and 85 percent now utilizing cloud storage with immutability capabilities. There is more work to be done, but this shows great progress in embracing a strategy that helps ensure that backups (instead of bitcoin) can be used to recover from ransomware.
Other individual data points pulled from the report include:
-
Backup repositories are a major target: In 96% of attacks, threat actors attempt to target backup repositories, highlighting the importance of robust backup security.
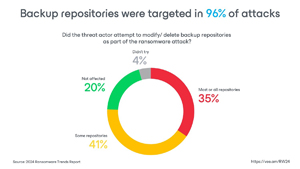 [Click on image for larger view.] Backup Repositories Were Targeted in 96% of Attacks (source: Veeam).
[Click on image for larger view.] Backup Repositories Were Targeted in 96% of Attacks (source: Veeam).
-
Ransom is just a portion of the cost: While paying the ransom is a significant cost (32% of the financial impact), other factors like lost productivity and brand reputation take a bigger toll (68%).
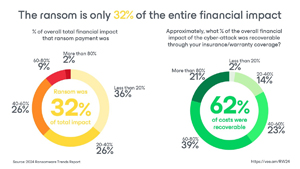 [Click on image for larger view.] Ransom Is Only 32% of Entire Financial Impact (source: Veeam).
[Click on image for larger view.] Ransom Is Only 32% of Entire Financial Impact (source: Veeam).
-
Data recovery challenges: A significant portion of data (43%) is not recoverable after a ransomware attack, even after paying the ransom.
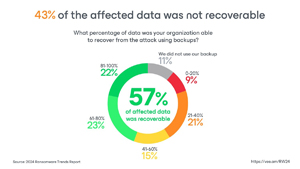 [Click on image for larger view.] 43% of Affected Data Not Recoverable (source: Veeam).
[Click on image for larger view.] 43% of Affected Data Not Recoverable (source: Veeam).
-
Importance of clean backups: Only 37% of organizations ensure their backups are clean (free of malware) before restoring data, increasing the risk of re-infection.
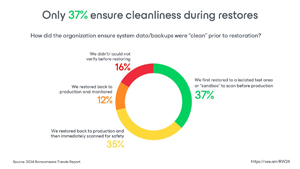 [Click on image for larger view.] Only 37% Ensure Cleanliness During Restores (source: Veeam).
[Click on image for larger view.] Only 37% Ensure Cleanliness During Restores (source: Veeam).
-
Recovery options beyond original infrastructure: Organizations can recover data to cloud infrastructure (86%) or other on-premises servers (75%) in case the original servers are compromised.
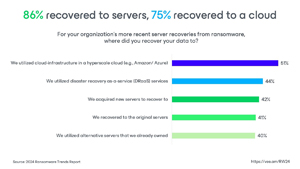 [Click on image for larger view.] 86% Recovered to Servers, 75% to Cloud (source: Veeam).
[Click on image for larger view.] 86% Recovered to Servers, 75% to Cloud (source: Veeam).
-
Importance of collaboration: IT and security teams often lack alignment (63% need improvement), hindering overall preparedness.
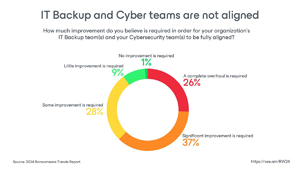 [Click on image for larger view.] IT Backup/Cyber Teams Not Aligned (source: Veeam).
[Click on image for larger view.] IT Backup/Cyber Teams Not Aligned (source: Veeam).
-
Third-party involvement during remediation: Many organizations involve backup vendors (42%), security vendors (42%), and forensics specialists (42%) during remediation.
 [Click on image for larger view.] Third Parties Involved During Remediation (source: Veeam).
[Click on image for larger view.] Third Parties Involved During Remediation (source: Veeam).
-
Wiping and restoring infected servers may not be an option: Due to various reasons, a significant portion (31%) of infected servers cannot be simply wiped and restored.
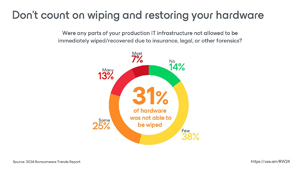 [Click on image for larger view.] Wiping and Restoring (source: Veeam).
[Click on image for larger view.] Wiping and Restoring (source: Veeam).
-
Immutable backups gain traction: A growing number of organizations are using immutable backups (resistant to tampering) — 85% in cloud storage and 75% on disk.
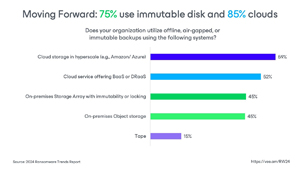 [Click on image for larger view.] 85% Use Immutable Cloud Storage (source: Veeam).
[Click on image for larger view.] 85% Use Immutable Cloud Storage (source: Veeam).